ASSESSMENTS
A cybersecurity assessment identifies various information assets that could be harmed by a cyber attack, as well as the numerous threats that could influence those assets.
Don't know where to start?
Use our evaluation services to figure out the best way and plan your cybersecurity journey
Vulnerability Assessments and pen-testing
Vulnerability scanners notify businesses of pre-existing problems in their environments and where they can be found.
Penetration tests try to exploit those findings in order to discover whether unauthorized access or other malicious activity is possible, as well as to assess which flaws that pose a threat to the organization.

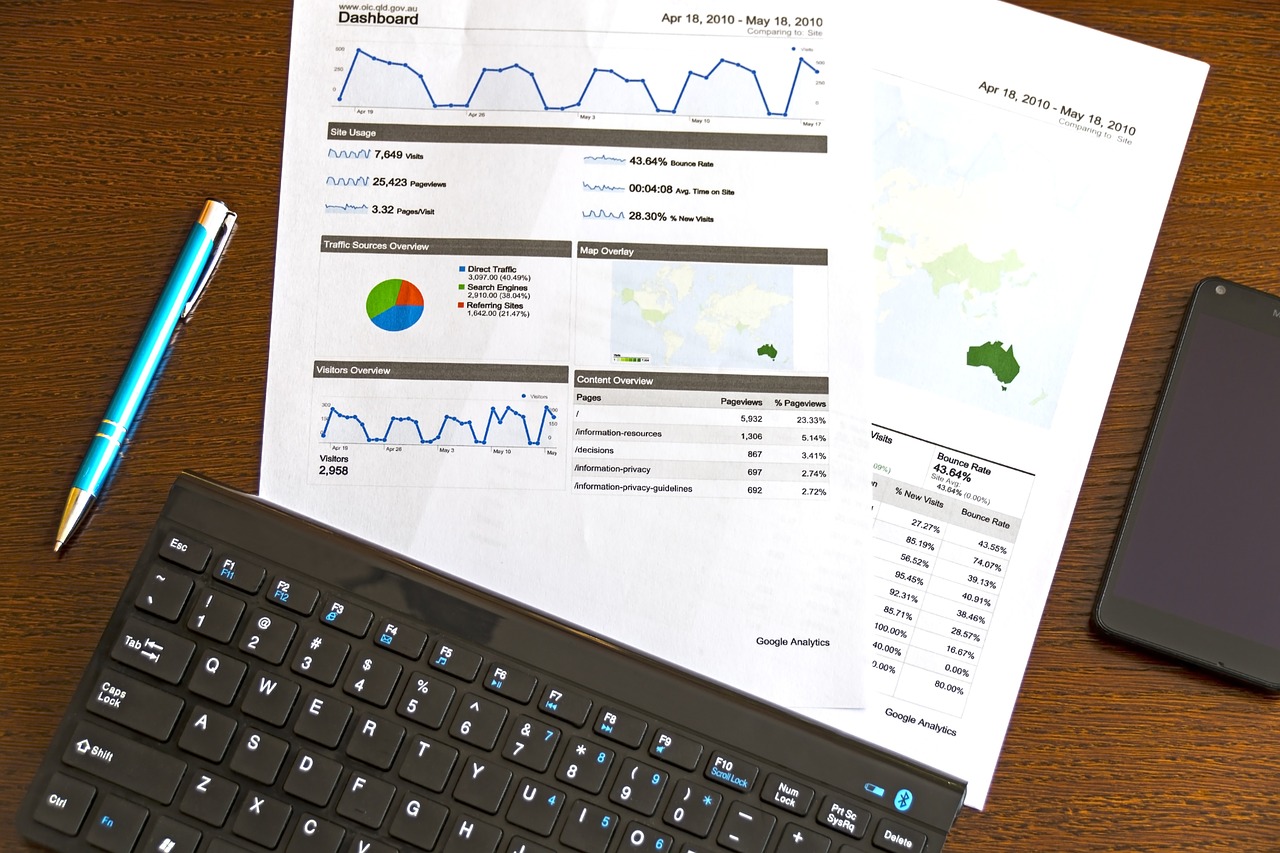
Security Posture Assessments
An examination of a system’s, network’s, or organization’s security posture is known as a security posture assessment.
It is computed using resources such as personnel, hardware, and software capabilities, as well as a change mechanism which is implemented when an actual breach happens.
Threat Simulation
Threat simulation is an advanced computer security testing method. These simulations identify vulnerabilities in security environments by mimicking the likely attack paths and techniques used by malicious actors.


Application Security
Tasks that introduce a secure software development life cycle is Application security. Its ultimate purpose is to improve security practises and, as a result, detect, repair, and, ideally, avoid security flaws in applications.
Cloud and Container Security
Cloud security encompasses a wide range of rules, technologies, applications, and controls that are used to safeguard virtualized IPs, data, applications, services, and the associated cloud computing infrastructure.
Container security is the process of implementing security tools and policies to ensure that everything in your container is functioning properly, including infrastructure protection, software supply chain protection, runtime protection, and everything in between.

Compliance & Auditing
In the context of cybersecurity, compliance refers to the development of a programme that provides risk-based controls to safeguard the integrity, confidentiality, and accessibility of data stored, processed, or transferred.
Cyber security standards, guidelines, and policies are the focus of a cyber security audit. It also ensures that all security controls are optimized and compliance standards are met.
Network Security
The policies, techniques, and practises used to prevent, detect, and monitor unauthorised access, misuse, modification, or denial of a computer network and network-accessible resources are referred to as network security.

Let’s get started
Talk to us to understand our approach and steps involved to complete an assessment

© 2025 All Rights Reserved.

